Istio Ingress Gateway using Network load balancer on EKS
This article discusses the need and steps to create an network load balancer in AWS for an EKS cluster using Istio
Terminology
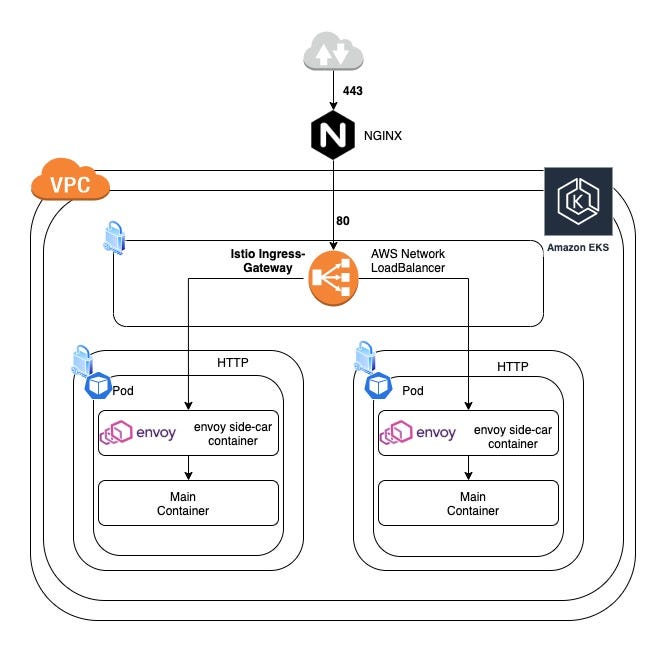
EKS is the Managed Kubernetes Service available on AWS and applications running inside the cluster are usually accessed from outside the cluster via an Ingress Gateway which sits at the edge of the cluster. This gateway uses a load balancer which can be a Classic (CLB), Application (ALB), or Network (NLB) load balancer provided by AWS.
Istio is an open-source independent service mesh that provides the fundamentals you need to successfully run a distributed microservice architecture. By default, istio creates a service with a publicly accessible classic load balancer (ELB). However, there are times where we only want access from our internal network or a network we are connected to via a secure VPN.
The following are a summary of the steps involved, which I collated from various sources on the web. Please note the official documentation takes precedence and the following steps are only a pointer to get you started ..
Need
There may be requirements to expose applications running inside the k8s cluster internally only i.e. not exposed via the internet and/or accessible only to certain security group, In our case the security group in which Nginx is exposed over the internet. To access these services from On-prem servers you may need to open certain firewall rules. To add firewall rules you may need static IP address to be attached with your load balancer. Here we can use the feature from Network load balancer which comes with static IP address.
Steps to create Internal Ingress gateway
Resources that are needed for the ingress gateway:
- istioctl
Download and setup istioctl on your workstation using the release page: https://github.com/istio/istio/releases
2. Unzip tar file
3. Now update the below file to create Internal Network load balancer using istioctl.
cd istio-{RELEASE_TAG}

4. Save the file and run below command to setup istio ingress gateway within EKS cluster:
istioctl install — set profile=demo — charts=./manifests/ \
— set components.cni.enabled=true \
— set components.cni.namespace=kube-system
5. Check the AWS console — EC2/Load Balancers section to see if the NLB has been provisioned with scheme Internal.
6. To remove above setup from cluster run this command:
istioctl manifest generate — set profile=demo — charts=./manifests/ \
— set components.cni.enabled=true \
— set components.cni.namespace=kube-system | kubectl delete -f -
Steps to create External Ingress gateway using EIP
- istioctl
Download and setup istioctl on your workstation using the release page: https://github.com/istio/istio/releases
2. Unzip tar file
3. Now update the below file to create External Network load balancer using istioctl and Elastic IP.
cd istio-{RELEASE_TAG}
4. Get the list of Association ID’s for Elastic IP addresses which needs to be associated. with Ingress gateway NLB.

5. 4. Save the file and run below command to setup istio ingress gateway within EKS cluster:
istioctl install — set profile=demo — charts=./manifests/ \
— set components.cni.enabled=true \
— set components.cni.namespace=kube-system
5. Check the AWS console — EC2/Load Balancers section to see if the NLB has been provisioned with EIP attached.
6. To remove above setup from cluster run this command:
istioctl manifest generate — set profile=demo — charts=./manifests/ \
— set components.cni.enabled=true \
— set components.cni.namespace=kube-system | kubectl delete -f -
Please leave comments if this was helpful, or if you have questions, or if you have a better way to implement this.
Thank you for reading.
